Understanding XML Bombs: A Deep Dive into Vulnerabilities, Attacks, and Prevention
Table of Contents
- Introduction to XML and Its Role in Modern Applications
- What is an XML Bomb?
- How XML Bombs Work
- Real-World Examples and Case Studies
- Impact of XML Bomb Attacks
- Unsafe Treatment of XML Macros
- Detecting and Preventing XML Bombs
- Best Practices for Safe XML Parsing
- Secure Coding Standards for XML Processing
- XML Bombs in Different Languages and Frameworks
- Tools for Analyzing XML Files
- Developer and DevOps Perspectives
- Role of WAFs and Intrusion Detection Systems
- XML Bombs vs. Other Injection Attacks
- Future Threats and the Evolution of XML Security
- Conclusion and Key Takeaways
- References
1. Introduction to XML and Its Role in Modern Applications
Extensible Markup Language (XML) is a widely-used format for exchanging structured data across different systems. From configuration files to web services and SOAP APIs, XML plays a critical role in numerous applications.
However, its flexibility can become a double-edged sword. Improperly handled XML input can expose systems to a range of security vulnerabilities—including the notorious “XML Bomb.”
2. What is an XML Bomb?
An XML Bomb is a form of Denial-of-Service (DoS) attack that exploits the way XML parsers process XML input. By nesting XML entities within one another in an exponential manner, attackers can cause the parser to consume massive amounts of memory and CPU, potentially crashing the system.
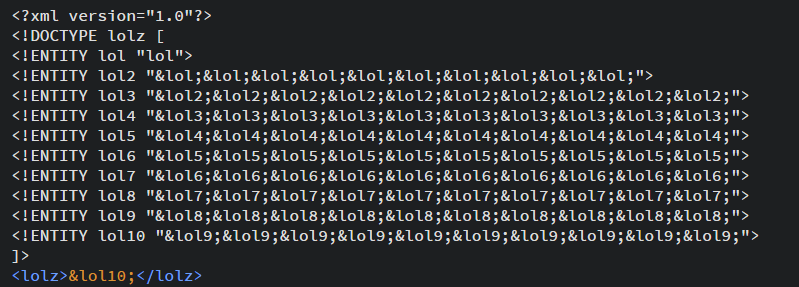
The Classic Billion Laughs Attack
This notorious XML bomb attack uses recursive entity expansion:
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
...
]>
<lolz>&lol9;</lolz>
Each expansion multiplies the data, eventually consuming gigabytes of memory.
3. How XML Bombs Work
XML bombs leverage the concept of entity expansion. Here’s how it unfolds:
- Entity Declaration: A small entity is defined.
- Recursive Expansion: Larger entities reference smaller ones repeatedly.
- Parser Exhaustion: When the XML file is parsed, the system tries to resolve all the entities, using up CPU and memory.
- System Crash: The service becomes unresponsive or crashes.
4. Real-World Examples and Case Studies
Adobe ColdFusion
In 2013, ColdFusion was found vulnerable to XML DoS due to entity expansion. Attackers could bring down servers with a single request.
Microsoft Services
Several Microsoft services were also discovered to be vulnerable to XML bombs due to improper parsing logic.
Open-Source Libraries
Popular libraries like Xerces, libxml2, and others had issues related to XML entity handling.
5. Impact of XML Bomb Attacks
- Downtime: System or application becomes unavailable.
- Resource Drain: High CPU and memory usage.
- Reputation Damage: If critical systems go offline, user trust may erode.
- Financial Loss: Prolonged downtime can lead to revenue loss.
6. Unsafe Treatment of XML Macros
XML Macros are often used for dynamic content or configurations. When these macros are processed without sanitization, they can be exploited:
- Dynamic Entity Expansion
- Command Injection via Macros
- Backdoor Configurations
Many developers overlook the dangers of including unvalidated macros in XML files. This leads to XML Injection, external entity expansion (XXE), and bomb vulnerabilities.
7. Detecting and Preventing XML Bombs
Detection Techniques:
- Monitor memory and CPU usage patterns.
- Use static code analysis to catch unprotected entity parsing.
- Log and audit XML parsing behavior.
Prevention:
- Disable external entity parsing (XXE).
- Set strict limits on XML depth and size.
- Use safe XML libraries with protection against recursive expansion.
8. Best Practices for Safe XML Parsing
- Always validate XML input against schemas (XSD).
- Avoid DTDs if not needed.
- Use streaming parsers like SAX instead of DOM.
- Apply sandboxing and resource limits.
9. Secure Coding Standards for XML Processing
Many security standards provide guidelines for safe XML processing:
- OWASP XML Security Cheat Sheet
- NIST Secure Coding Guidelines
- CWE-776: Improper Restriction of Recursive Entity Expansion
10. XML Bombs in Different Languages and Frameworks
- Java: Apache Xerces, JAXB – disable
external-general-entities. - Python: lxml, xml.etree – restrict or sanitize input.
- PHP: libxml – disable entity loading.
- .NET: XmlDocument and XmlReader – use secure settings.
11. Tools for Analyzing XML Files
- Burp Suite: XML payload testing.
- Static Code Analyzers: SonarQube, Fortify.
- Command-Line:
xmllintwith options to detect expansion. - Custom Parsers: Build XML validators with security checks.
12. Developer and DevOps Perspectives
Developers need to sanitize input, while DevOps teams should monitor runtime behavior:
- Use containerization to isolate XML parsers.
- Monitor logs for suspicious XML patterns.
- Enforce security policies via CI/CD pipelines.
13. Role of WAFs and Intrusion Detection Systems
Web Application Firewalls (WAFs) can detect and block malicious XML payloads.
IDS systems can flag abnormal traffic patterns, helping detect slow-burning XML bomb attacks.
14. XML Bombs vs. Other Injection Attacks
XML Bombs are often confused with:
- XXE (XML External Entity Injection)
- XPath Injection
- SOAP Injection
Key difference: XML bombs are aimed at denial of service, while others often target data theft or control.
15. Future Threats and the Evolution of XML Security
- AI-Generated Payloads: Crafting smarter XML bombs.
- Hybrid Attacks: XML bombs combined with XXE or SSRF.
- Cloud Vulnerabilities: Shared environments may amplify damage.
Staying updated with secure parser libraries and community advisories is key.
16. Conclusion and Key Takeaways
XML is powerful—but with power comes responsibility. Developers, sysadmins, and DevOps engineers must:
- Understand the dangers of XML bombs.
- Sanitize all XML input.
- Use secure parsing libraries.
- Monitor and audit systems constantly.
Being proactive in XML security can save your infrastructure from potentially devastating DoS attacks.
17. References
- OWASP: https://owasp.org/www-project-cheat-sheets/cheatsheets/XML_Security_Cheat_Sheet.html
- CWE-776: https://cwe.mitre.org/data/definitions/776.html
- NIST Secure Coding: https://csrc.nist.gov/
- MSDN XML Security: https://learn.microsoft.com/
- XML Bomb GitHub examples: https://github.com/search?q=xml+bomb