
Similar Posts
How Git History Reveals Your Riskiest Code
ByAdilI. Introduction: The Critical Gap in Resilience For years, I’ve managed projects where everyone knew which files were the maintenance nightmares—the ones where a small change led to a two-day debugging session. As engineers, we invest heavily in Code Correctness — we run linters, use SCA tools, and write comprehensive unit tests. However, these traditional…

Deploy an Astro Blog with Cloudflare Pages and Porkbun
ByAdilTired of slow, clunky blog setups that cost more than your morning coffee? The modern web offers a powerhouse trio for building and deploying content-focused websites that are ridiculously fast, globally distributed, and wonderfully free. This is the JAMstack dream, realized. In this guide, we’ll walk through the entire process of creating a high-performance blog…
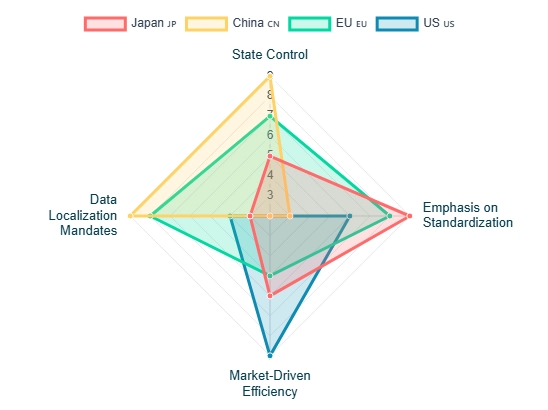
In 2025, AI regulations were established in four major global regions.
ByAdilGreetings from the island nation of Japan. We often observe the complex, multi-layered strategies of the major global powers (Japan, China, the EU, and the US) with a kind of detached, yet deeply involved, professional interest. The concept of Sovereign Cloud and AI Governance is essentially the high-stakes game of ensuring that while we all…

Ubisoft continues its partnership with mental health charity Safe In Our World with new Good Game Playbooks to promote positive online play and protect from disruptive behaviour
ByAdilUbisoft has announced new editions of its Good Game Playbooks to promote positive play in young gamers. 🎬 Watch the Video

The Samsung Galaxy S25 Edge might disappear next year, so grab this record-low Black Friday price while you still can
ByAdilThe Samsung Galaxy S25 Edge is rumored to be replaced by a regular Galaxy S26 Plus next year, so this fantastic Amazon Black Friday deal could be a good buy while you have the chance. 🎬 Watch the Video

Prime Video ad tier breaks astonishing new subscriber record – but I’m close to cancelling the Amazon service
ByAdilPrime Video has announced how many subscribers its ad-supported tier is reaching, but they might just be losing one. 🎬 Watch the Video