Solving AI’s energy challenge: sustainable data centers for a competitive UK future
AI’s energy appetite is increasing rapidly. Traditional disk storage is a major, often overlooked, energy drain.

AI’s energy appetite is increasing rapidly. Traditional disk storage is a major, often overlooked, energy drain.

All the ways to watch UCI World Tour 2026 live streams online and from anywhere, as 18 teams compete across 36 events around the world.

AI agents are getting better at writing code, answering questions, and even managing workflows. But there’s a core limitation most developers hit quickly: AI models don’t remember context well enough to behave like real agents. This is exactly the problem Model Context Protocol (MCP) is designed to solve. In this post, we’ll break MCP down…
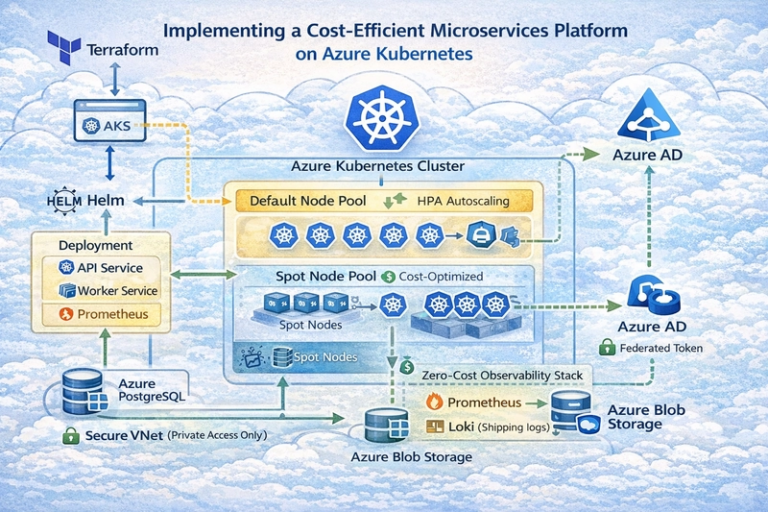
Terraform, Autoscaling, Spot Capacity, and Workload Identity This article focuses on implementation details. Architectural rationale and cost trade-offs are covered in Part 1. Scope and Assumptions This post assumes: Familiarity with Kubernetes fundamentals Comfort reading Terraform and Helm Interest in operating systems, not just deploying them The platform runs on Azure Kubernetes Service, provisioned with…

I spent three hours last week helping a junior developer debug their project, only to realize they had 47 different npm packages, 8 VS Code extensions they’d never used, and three separate testing frameworks installed. When I asked why, they said, “I thought I needed all of them to be a real developer.” Sound familiar?…

The Apple Watch SE 3 already represents sensational value for Apple fans, but it’s now dropped to a new all-time low, making it a bonafide bargain.

We uncovered a sneaky way to watch A Knight of the Seven Kingdoms for FREE – from anywhere in the world, without coughing up for a Premium streaming subscription.

Introduction: Understanding Git and Git-hub If you are a beginner, it’s important to understand the difference between the two tools, git and git-hub: So, what’s Git? What’s it used for? Basically, Git is a popular version control system which is used to>track code changes coding collaborations between developers tracking who made the changes On the…

Hi there, it’s me again. Today, I want to share a great (and painful) experience I had while deploying a product to production. My team and I were working on a very simple product. Its only responsibility was to register users — nothing complex, no heavy business logic. Simple, right? Well… not exactly. The DevOps…

In modern backend systems, rate limiting is essential. Without it, APIs are exposed to abuse, resource exhaustion, and unfair usage. That’s why I built a production-ready, thread-safe rate limiter library in Go, based on the Token Bucket algorithm. Why Token Bucket? I chose the Token Bucket algorithm because it: Allows controlled bursts of traffic Provides…