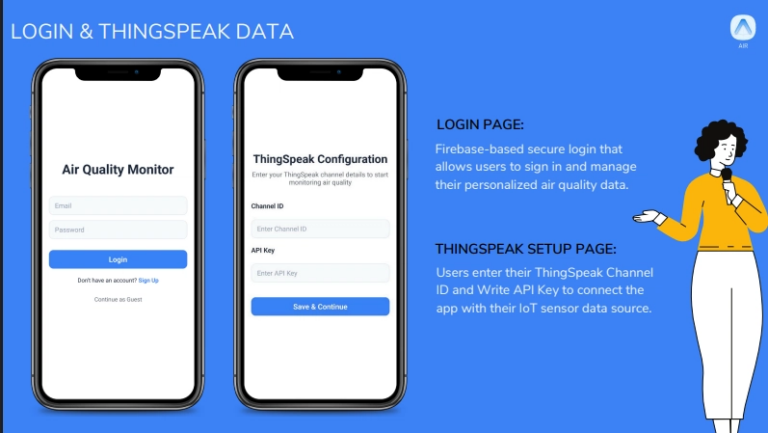
How I Built a Self-Feeding SEO Engine with GPT-4o Vision + Next.js 15
Two weeks ago, I launched an ai tattoo generator called TattooRed. Today, I have 200 pages generated and 15 indexed by Google. But here’s the interesting part: users generate the content, GPT-4o Vision enriches it, and Next.js 15 serves it—automatically. The architecture is designed to scale from 0 to 100K+ pages at $0.006 per page….