Lanterns won’t burn bright on HBO Max in early 2026 as DC comic book show suffers release window set-back
HBO has confirmed a big rumor about Lanterns’ launch window – and it’s not good news for Green Lantern fans.

HBO has confirmed a big rumor about Lanterns’ launch window – and it’s not good news for Green Lantern fans.

Save big on some of TechRadar’s top rated home office picks in Flexispot’s Black Friday sale and get up to 80% off.

Here’s where you can get the best early Black Friday deals on the iPhone 16, iPhone 16 Plus, iPhone 16e, iPhone 16 Pro, and iPhone 16 Pro Max

Let’s implement a custom hook that mimics the behavior of React’s useState without using useState internally. This will involve using React’s underlying mechanisms, specifically leveraging a simple state management approach with a closure or a global store to maintain state across renders. Here’s a basic implementation of a custom useState-like hook: import React from ‘react’;…

Two weeks ago, I launched an ai tattoo generator called TattooRed. Today, I have 200 pages generated and 15 indexed by Google. But here’s the interesting part: users generate the content, GPT-4o Vision enriches it, and Next.js 15 serves it—automatically. The architecture is designed to scale from 0 to 100K+ pages at $0.006 per page….
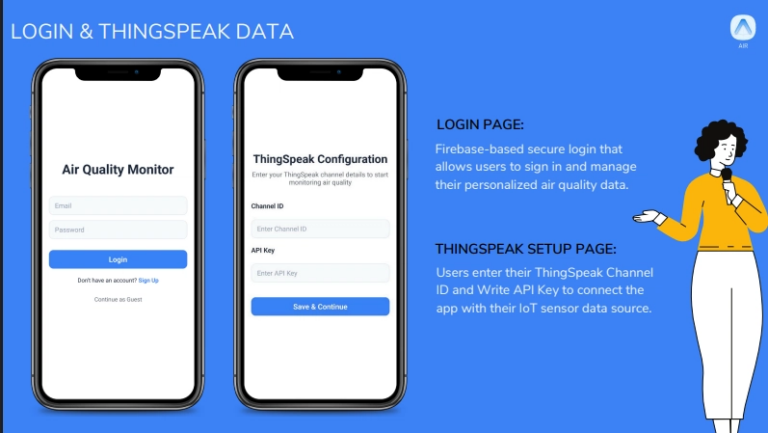
👥 Who Is It For? The AI AIR APP is designed for: Home users who want to monitor indoor air quality. Outdoor enthusiasts who care about pollution levels before stepping out. Researchers & developers experimenting with IoT sensors and environmental data. Health-conscious individuals who want personalized insights into air quality and wellness. If you have…

The fourth episode of Pluribus includes a big character reveal – here’s why they might be important to solving The Joining.

Black Friday OLED TV deals are now live, and there are incredible discounts to be had on 2025’s best OLED TVs.

Landman season 2 episode 2 reveals more about Tommy’s relationship with his parents, but when can we watch it?

This week, Google released Antigravity, their new agentic development platform. I’d been using Gemini CLI with GitHub’s Spec-Kit for a while already, running through the full spec-driven workflow from constitution to implementation. But something always felt incomplete about the implementation phase – like I was handing a meticulously written recipe to a chef who kept…