
Similar Posts
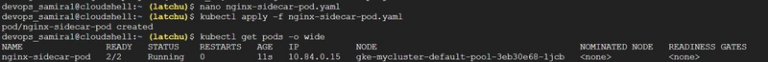
Scenario #2: Multi-container Pod (Sidecar pattern) for logging in Kubernetes
ByAdilThis one will show how multiple containers in a single Pod can share data and work together, just like microservices collaborating closely inside one unit. 🎯 Goal Create a multi-container Pod with: One main container running NGINX One sidecar container that tails NGINX access logs and prints them to its own stdout (mimicking a log…

Interpolate a Video from the First and Last Frames with Veo 3.1 and Nano Banana
ByAdilGoogle released Veo 3.1 with new features and one of them is using the first and last frames to interpolate a video. When leveraging the image generation of Gemini 2.5 Flash Image model (a.k.a Nano Banana), Veo 3.1 model can use the first and last images to generate a short video. This interpolation feature is…

Application of API Testing Frameworks in Java Introduction
ByAdilIntroduction In modern software development, API testing frameworks play a crucial role in ensuring that communication between services is reliable, consistent, and secure. APIs (Application Programming Interfaces) are the backbone of microservices architectures, and their stability directly affects the performance of entire systems. Frameworks such as RestAssured, Postman/Newman, and Karate allow developers to automate API…

How to watch New Zealand Kiwis vs Toa Samoa: free streams, TV channels for Pacific Cup 2025 Final
ByAdilAll the ways to watch the Pacific Cup Final between New Zealand Kiwis and Toa Samoa as they do battle at CommBank Stadium, Sydney. 🎬 Watch the Video

Philips Evnia 49M2C8900 QD-OLED review: A strong highlight among the greatest super ultrawide monitors
ByAdilOne of the most immersive displays I’ve used 🎬 Watch the Video

Like Spotify’s new Listening Stats upgrade? Here are 12 other great new features you may have missed this year
ByAdilSpotify Wrapped is about to arrive any day. This is our review of Spotify’s year of new features. 🎬 Watch the Video