Learn About This Vulnerability → Reflected XSS
Introduction
Web security is an increasingly important topic in the digital era, with numerous attack vectors threatening the confidentiality, integrity, and availability of online platforms. One particularly insidious threat is Cross-Site Scripting (XSS). Within this broad category, Reflected XSS stands out due to its prevalence and the subtlety with which it operates. This article will delve deeply into Reflected XSS, exploring what it is, how it works, real-world examples, detection techniques, and mitigation strategies, all aimed at helping developers, security professionals, and website owners protect their online assets.
What is Reflected XSS?
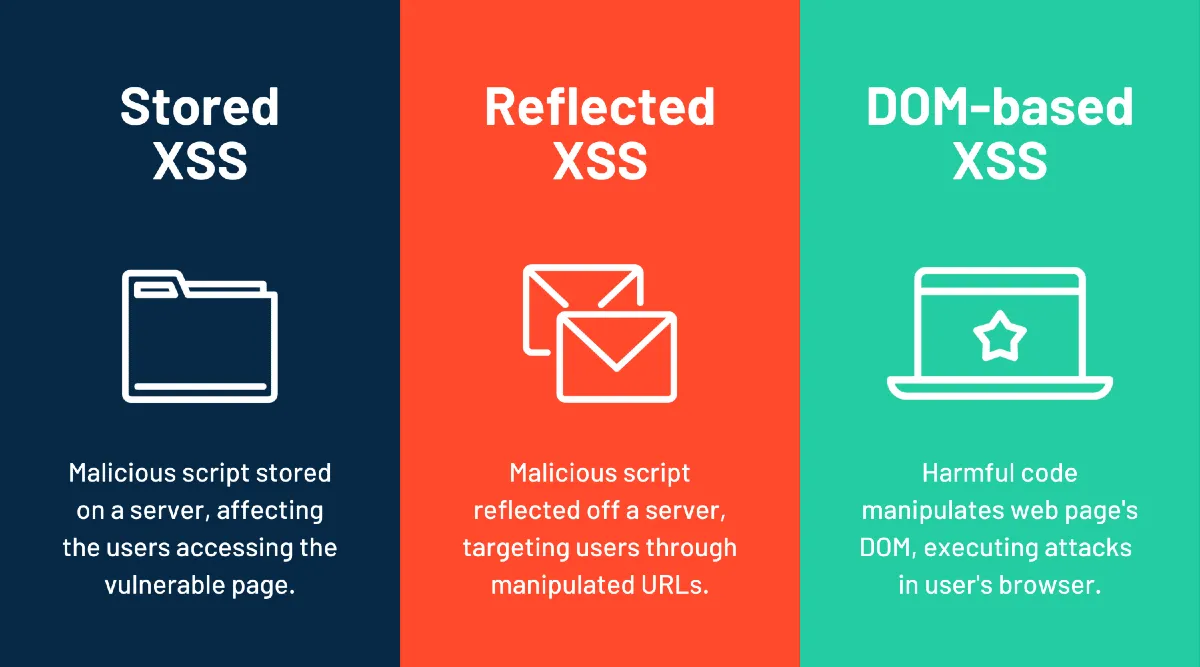
Reflected XSS, or Non-Persistent XSS, is a type of cross-site scripting attack where malicious scripts are reflected off a web server. Unlike stored XSS, where the payload is permanently stored on the target server (e.g., in a database), reflected XSS occurs when a malicious script is part of the request and is immediately included in the response.
Basic Mechanism
- User Sends Malicious Request: The attacker tricks the victim into clicking a specially crafted URL that includes malicious JavaScript as a parameter.
- Server Reflects Input: The server processes this request and reflects the input directly in the HTTP response, often in an error message, search result, or any dynamically generated content.
- Browser Executes Script: Since the response contains the malicious script, the browser executes it in the context of the trusted domain.
Common Injection Points
- URL parameters (e.g., search query inputs)
- Form inputs
- HTTP headers (e.g., User-Agent)
How Reflected XSS Works
To understand Reflected XSS better, let’s go through a concrete example.
Example Scenario
Consider a website with a search functionality:
https://example.com/search?q=test
The backend script simply reflects the query parameter back into the HTML response:
<h1>You searched for: test</h1>
If the application fails to sanitize input, an attacker could craft a URL like this:
https://example.com/search?q=<script>alert('XSS')</script>
If the server reflects this back without encoding or sanitization:
<h1>You searched for: <script>alert('XSS')</script></h1>
The browser will execute the script, causing a popup.
Impact of Reflected XSS
The potential damage caused by Reflected XSS can be severe. While it does not persist on the server, it can still:
- Steal cookies and session tokens
- Impersonate users
- Redirect victims to malicious websites
- Perform actions on behalf of users
- Log keystrokes
Real-World Consequences
In 2014, eBay was reported to have a Reflected XSS vulnerability that could be used to redirect users to phishing pages. Though the attack did not compromise eBay’s servers directly, it used eBay’s reputation to build user trust.
Detection Techniques
Detecting Reflected XSS involves both manual testing and automated tools.
Manual Testing
- Input Field Fuzzing: Manually enter payloads like
"><script>alert('XSS')</script>into input fields and check if they are reflected unescaped. - HTTP Header Manipulation: Modify headers like
Referer,User-Agent, etc., with script payloads.
Automated Scanners
- Burp Suite: Intercepts traffic and can automatically detect XSS vulnerabilities.
- OWASP ZAP: Open-source tool that scans for XSS among other vulnerabilities.
- Nikto: Web server scanner with basic XSS detection capabilities.
Mitigation Strategies
To prevent Reflected XSS, developers need to adopt a multi-layered approach.
1. Input Validation
Validate all inputs strictly. Ensure they match expected formats and lengths. However, validation alone is not enough.
2. Output Encoding
Encode output based on the context in which data appears:
- HTML Context: Convert
<,>,&,", and'to HTML entities. - JavaScript Context: Use safe JavaScript encoding to prevent breaking out of script blocks.
- Attribute Context: Properly quote and encode attributes.
3. Use Security Libraries
Frameworks and libraries often provide built-in XSS protection. Examples include:
- React: Automatically escapes variables in JSX.
- Angular: Uses context-aware escaping.
- Django Templates: Auto-escape HTML by default.
4. HTTP Headers
- Content-Security-Policy (CSP): Restrict sources from which scripts can be loaded.
- X-XSS-Protection: Enable browser’s XSS filter (though deprecated in modern browsers).
5. Avoid Dangerous Functions
Avoid using eval(), document.write(), and innerHTML with untrusted data. Use safer alternatives like textContent or DOM APIs.
6. User Awareness
Educate users not to click suspicious links and to verify URLs before entering credentials.
Penetration Testing for Reflected XSS
Penetration testers follow a structured approach:
- Reconnaissance: Identify endpoints reflecting user input.
- Payload Crafting: Test various payloads to see how the application handles them.
- Contextual Analysis: Determine the context of reflection (HTML, JS, Attribute, etc.).
- Bypass Techniques: Use encoding, concatenation, or obfuscation to bypass filters.
- Report Generation: Clearly document findings with proof of concept (PoC) URLs.
Browser-Based Protections
Modern browsers incorporate some XSS protection mechanisms:
- XSS Auditor (Chrome, deprecated): Blocked rendering of suspicious scripts.
- Trusted Types API: Helps enforce content safety policies.
Case Studies
Case Study 1: Reflected XSS in a Government Portal
A government website allowed search queries to be reflected in the page without encoding. An attacker crafted URLs that executed scripts stealing session tokens. Though the breach was contained quickly, it highlighted the importance of encoding.
Case Study 2: E-commerce Site with Open Redirection
A shopping site used URL parameters for redirects after login. The parameter was not validated properly, enabling XSS payloads. This was exploited to steal user sessions and personal data.
Evolving Threat Landscape
Reflected XSS has evolved. Today, attackers use more sophisticated payloads, often leveraging browser quirks, sandboxing failures, or user interaction to increase success rates.
XSS Challenges in SPAs and APIs
Modern single-page applications (SPAs) and APIs pose new challenges:
- SPAs may use client-side routing, increasing exposure to DOM-based XSS.
- REST APIs might reflect input in unexpected ways, requiring context-aware sanitization.
Conclusion
Reflected XSS remains a critical threat in web application security. While modern frameworks and browsers offer some protection, responsibility ultimately lies with developers and security teams. By understanding the mechanisms, diligently applying best practices, and regularly testing, it’s possible to build robust defenses against this common but dangerous vulnerability.
Resources
- OWASP XSS Prevention Cheat Sheet
- Mozilla Developer Network (MDN) – XSS
- Google Web Fundamentals: Security
- Burp Suite Documentation
This blog is a living document. As new threats and tools emerge, revisit this guide to stay up to date with best practices and cutting-edge defenses against reflected XSS.