Oops… I Locked Myself Out with UFW — Here’s How I Fixed It
Does “F” in ufw stand for Fired?
Let us find out:
WHAT IS UFW?
UFW firewall utility is used to set up rules and configurations for a server firewall. It uses IP tables to perform the setup. People primarily use it in Linux distros.
UFW stands for Uncomplicated Firewall
UFW is a common type of firewall used to configure firewalls on a server. The server could be a web server, a network server, etc.
The server network can be a home network, corporate, e-commerce or business, service provision network, or any type of dedicated server. This helps you configure certain services to specific ports, regulating access and also controlling how users/clients interact with your server resources.
You create the rules, and others follow them.
Why a UFW firewall?
- This firewall helps you with your security.
- Anyone can easily set up and manage the UFW firewall because it is simple. – It uses IPv4 or IPv6 (helping in access control and traffic control).
- Prevent intruders and limit breaches in your server.
- Helps in Logging accessed and blocked operations.
How to set up the UFW firewall.
Some Linux distributions, like Ubuntu and CentOS, come pre-installed.
Check if UFW is installed using this commands:
sudo apt install ufw
sudo yum install ufw // for CentOS
You can also preview the basic UFW settings:
vi /etc/default/ufw or cat /etc/default/ufw
Get access to more details about the UFW utility.
man ufw
Locked out ???
Check if you have any setup rules before running the firewall to prevent being locked out.
Check the status rules.
sudo ufw status verbose
You can also show the reports and the active listening ports:
sudo ufw show raw
sudo ufw show listening
I recently got locked out after not considering that I was using a dynamic IP from my network provider. I set up a rule to only let access from the current IP, which I checked at whatismyip.com.
After a change of network and the release of my IP configurations on my local machine, I tried to connect via SSH and well…, I was in total disbelief. The system didn’t allow my newly assigned IP in. I am now an intruder.
How I had set up my SSH connection rule:
sudo ufw limit from 192.168.1.1 to any port 22
LIMIT – It is used to protect from brute-force attacks (e.g., it will rate-limit repeated connections). This limits one user per server connection with the same IP.
UFW Default Policies->
- Control incoming and outgoing access requests to the server.
sudo ufw default deny incoming
sudo ufw default allow outgoing
- Verify that applications are functioning properly and accessing the server according to the established rules and configurations.
sudo ufw app list
sudo ufw allow 'OpenSSH' // allows incoming connections to the OpenSSH service, by name.
These applications or services are stored in “/etc/ufw/applications.d”
Here are Some advanced UFW firewall rules and Tips.
- It is advisable to set up from scratch by resetting the rules. This disrupts any of the rules. When done, now set up manually.
sudo ufw reset
- If you do not want to start the firewall on startup, you should always disable the rules before exiting your machine. You can easily do this by stopping the firewall process from running:
sudo ufw disable
sudo systemctl stop ufw (sets and stops the service processes of ufw)
Set the rules first, then activate. .
The most common example rules and commands used for UFW firewall.
The system stores the default configurations at /etc/default/ufw.
Here are sample rules:
1. Allow requests like HTTP, SSH, ftp, https.
sudo ufw allow ssh
- You can also use their daemon ports for this configuration, like for SSH.
sudo ufw allow 22
2. Allow IP access or Block access.
sudo ufw allow from 123.08.01.01 to any port 443
- You can block access of a certain user to certain services
sudo ufw deny from 123.08.01.01 to any port 22
- Allow using subnets
sudo ufw allow from 123.08.01.01/24
- Allow an IP using a certain protocol
sudo ufw allow from 192.168.0.4 to any port 22 proto tcp
3. Delete rules.
First, list the rules.
sudo ufw status numbered
Then delete the rule by indexing it with its number;
sudo ufw delete rule 8 //(8 is the number of the rule.)
You can also delete using this approach.
sudo ufw delete allow 22
4. Permit Logging.
Enable logging:
sudo ufw logging on
Disable Logging:
sudo ufw logging off
5. Setup the Rules.
When done setting up,
Start the ufw firewall.
sudo systemctl start ufw
Then, start the services and implement the firewall rules.
sudo ufw enable
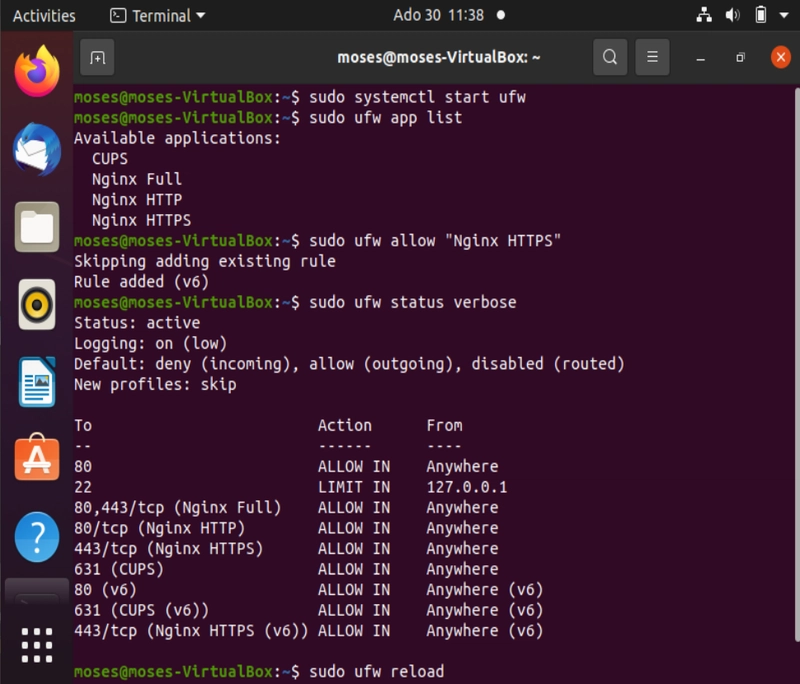
Alternatively, you can reload without starting or exiting the firewall.
sudo ufw reload
How to fix being locked out of UFW firewall.
This involves resetting the firewall. How do you reset a firewall if you have no access to it?
let us look at this concept first from the server architecture.
A server has a default port of access. That is port 22. When there is no permission to access, you can no longer ping the server or communicate with it.
Here is how to gain access depending on the various states of your server and services.
1. Console access. – Cloud service providers have a serial console, which is mostly web-based. It helps you log in to your server without SSH. They offer even server management tools for use. Look for direct access to the server.
When logged in, update your SSH rule.
sudo ufw allow ssh
You can also list the rules and then delete the rule number.
2. Rescue mode. – Some cloud service providers and VPS service providers have a rescue mode that helps you boot into your OS.
In technical terms, there is a “safe mode” in some OS platforms that helps you gain root access to the minimal setup of your OS.
The service providers offer you safe credentials for you to SSH into your secure rescue OS.
You then mount your real disk and access your server system as root.
mkdir /mnt/server
mount /dev/sda1 /mnt/server
chroot /mnt/server
When this fails or breaks, contact your service provider with your server details. Different companies have different ways of letting you access the server as root.
3. Reboot. – This applies to local servers where one can gain physical access.
Reboot, uses a keyboard or a mouse to log in. When logged in, access the terminal and change the rules.
When all the processes above are done, don’t forget to reload.
Reload UFW :
sudo ufw reload
NB: Before setting up and proceeding to activate a firewall, review your settings.
ufw show added
*UFW TIP *
If you like using graphical user interfaces, you can use the GUFW (Graphical Uncomplicated Firewall). Especially if you are a beginner.
sudo apt install gufw
Conclusion
UFW is an uncomplicated firewall interface for managing iptables rules. Serving as a gatekeeper, it is a crucial security feature in Linux. It works alongside the services being provided by our servers. It serves as an alternative to Firewalld(A dynamic firewall management tool), NFtables(supports IPv4 and IPv6 filtering), and IPTables(Mostly for network traffic with IPv4).
🔗 Follow Me on Socials and Let us link Up:
GitHub: @mosesmorrisdev
LinkedIn: Moses-Morris
Twitter: @Moses_Morrisdev
Facebook: Moses Dev