
Similar Posts

Why Your AI Agents Need a Shell (And How to Give Them One Safely)
ByAdilClaude Code changed how I think about agent architecture. It outperforms agents loaded up with 50 different MCP servers and custom integrations, and under the hood it’s remarkably simple. No tool sprawl. No massive schema definitions eating up context. Just a filesystem and bash. The AI community is starting to piece together why this works…
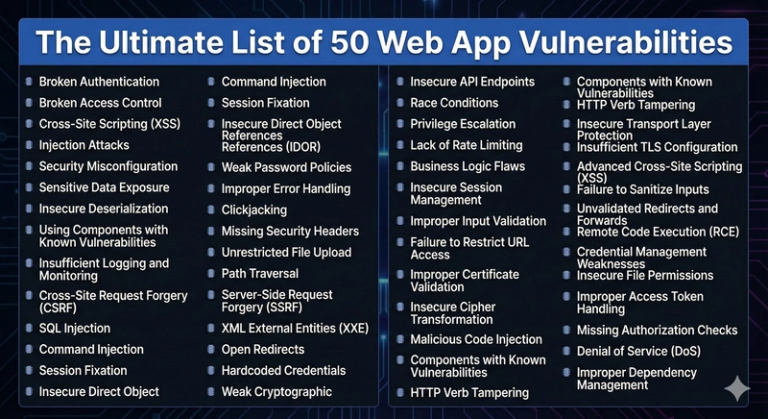
50+ Common Web Application Vulnerabilities Explained
ByAdilModern organizations increasingly rely on cloud-based platforms to deliver seamless digital experiences. While this improves agility and scalability, it also increases exposure to cyber threats. Even a single web application vulnerability can lead to data breaches, operational disruption, and loss of customer trust. Attackers actively exploit weaknesses in access control, authentication, APIs, and outdated components,…

The Invisible Hand That Fed Us
ByAdilA few days ago, I learned that Tailwind laid off 75% of their workforce. Their framework is everywhere now, in every frontend project, every prototype, every AI-generated landing page. More popular than it’s ever been. And yet. I thought very hard about it. There used to be a journey. You’d hear about a library from…

What is the release date for The Boyfriend season 2 episodes 1-6 on Netflix?
ByAdilIt’s been a whole year since Netflix’s surprise dating show hit first aired, and now it’s back. But when do the first batch of The Boyfriend season 2 episodes drop? 🎬 Watch the Video

I tested Ulefone’s loudest rugged phone – but while the RugKing offers exceptional value, there are limitations I can’t overlook
ByAdilThe Ulefone RugKing is a lightweight, rugged design ideal for those who need a tough device occasionally. 🎬 Watch the Video

Idle infrastructure might cause your next breach – here’s how to stop it
ByAdilWhat CISOs can do to secure inactive systems and overlooked storage before attackers exploit them. 🎬 Watch the Video