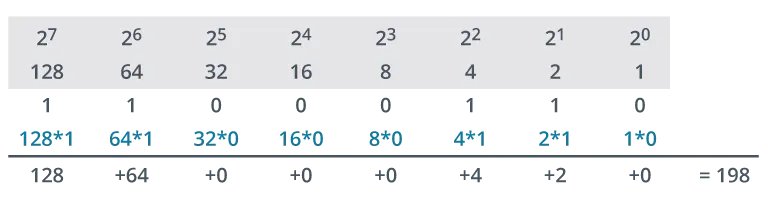CompTIA Network+ N10-009 Notes: A Simple Guide to IPv4
Preamble:
This space will be utilized to synthesize my notes and help improve my learning process while I study for the CompTIA Network+ N10-009 certification exam. Please follow along for more Network+ notes and feel free to ask any questions or, if I get something wrong, offer suggestions to correct any mistakes.
The core purpose of IP (Internet Protocol) is to allow different computer networks to communicate with each other, forming a larger network called an internetwork. This is why some data packets, addressed to devices on remote networks, must be forwarded through one or more intermediate systems (like routers) that create pathways between networks.
In this lesson, you’ll learn the basic principles of how IPv4 distinguishes between devices on the same local network and those on remote networks.
The Format of an IPv4 Address
Networks need a way to uniquely identify each network and each individual device, or host, within that network.
At the Data Link layer (Layer 2 of the OSI model), a network interface is identified by its MAC (Media Access Control) or hardware address. This type of address is only used for local delivery of data frames.
At the Network layer (Layer 3), IP source and destination addresses are used to forward data packets to the correct destination. An IP address provides two key pieces of information:
- The Network ID: This number is shared by all hosts on the same IP network.
- The Host ID: This number uniquely identifies a specific device within a network.
32-bit IPv4 Addressing
An IPv4 address is 32 bits long. In its raw, binary form, it looks like this:
11000110001100110110010000000001
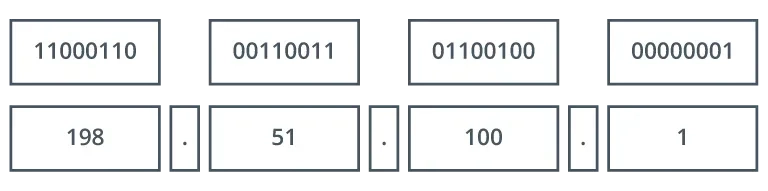
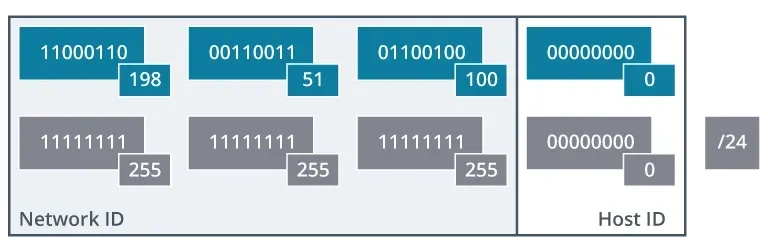
To make this easier for people to use, the 32 bits are divided into four groups of 8 bits, each group known as an octet.
11000110 00110011 01100100 00000001
We then convert each octet to a decimal value, separating them with a period. This is called dotted decimal notation. Converting the example above gives us:
198.51.100.1
Binary/Decimal Conversion
Understanding how to convert between binary and decimal is crucial. Here’s how it works:
In base 2 (binary), digits can only be a 0 or a 1. The place values are powers of 2: 20=1, 21=2, 22=4, 23=8, 24=16, 25=32, 26=64, and 27=128.
To convert a binary octet like 11000110 to decimal, you simply add the place values where there is a ‘1’.
- 128+64+0+0+0+4+2+0=198
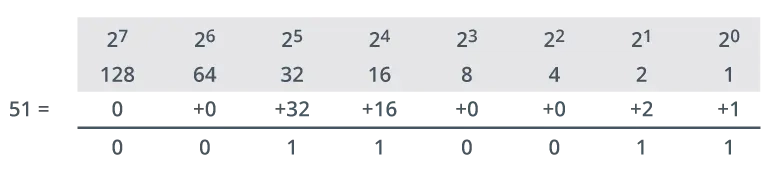
You can use the same method to convert from decimal to binary. For example, to convert the number 51, you find the powers of two that add up to 51. You would place a ‘1’ in those positions and a ‘0’ in the others.
- 32+16+2+1=51
- The binary representation would be:
00110011
Theoretically, an IPv4 address can be any value between 0.0.0.0 and 255.255.255.255. However, some addresses are not allowed or are reserved for special use.
Recommended Resource: For a deeper dive into binary math, check out Professor Messer’s video: https://youtu.be/94dcHJfEAIo?si=nHUgeGN03wFsSED7
Network Masks
An IP address holds both the network ID and the host ID. In IPv4, a 32-bit network mask (or netmask) is used to separate these two parts. The mask essentially “hides” the host ID portion, revealing only the network ID.
A network mask has the same number of bits as an IPv4 address (32 bits). Anywhere there is a binary ‘1’ in the mask, the corresponding bit in the IP address is part of the network ID. The ‘1’s in a mask must always be contiguous (all in a row).
Valid Mask: 11111111 11111111 11111111 00000000Invalid Mask: 11111111 00000000 11111111 00000000 (The ‘1’s are not contiguous)
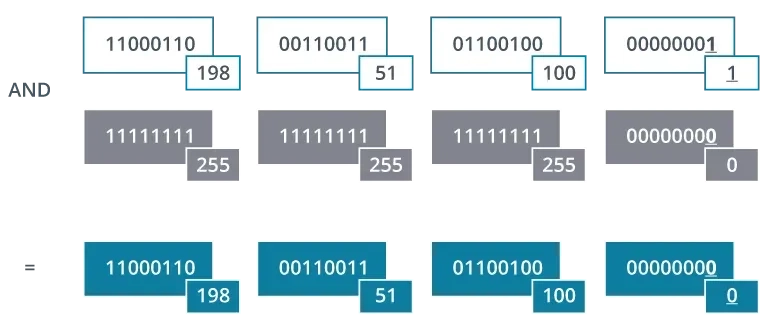
To find the network ID of any IP address, you use a logical operation called ANDing. When you AND two bits together, the result is ‘1’ only if both original bits were ‘1’. In all other cases, the result is ‘0’.
This operation allows the computer to find the network ID by comparing the IP address with the network mask.
Slash Notation
Instead of using the long dotted decimal mask like 255.255.255.0, you can use prefix or slash notation. The prefix is simply the number of bits set to ‘1’ in the mask. So, a mask with 24 ‘1’s can be written as /24. The network can then be referred to as 198.51.100.0/24.
The default masks for IPv4 addresses align with octet boundaries, so the decimal values are always 255 or 0.
Subnetting
The default addressing scheme uses whole octet boundaries for the network mask, which can be inflexible. Subnetting was created to divide large networks into smaller, more manageable parts called subnets.
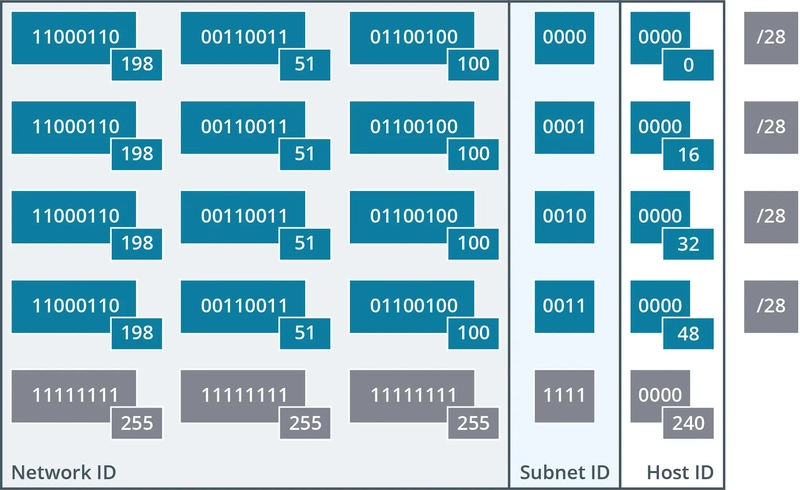
Subnetting adds a third hierarchical level: a network ID, a subnet ID, and a host ID. To create a subnet, you ‘borrow’ bits from the host portion of the IP address and use them for the subnet address.
This leaves fewer bits for the host ID, which means each subnet will have fewer available host addresses.
- It’s important to remember that only one mask is applied to an IP address on an interface.
- External networks continue to address the entire network by its original network ID (e.g.,
198.51.100.0/24). - Hosts within the network use the longer subnet mask to differentiate between the subnets.
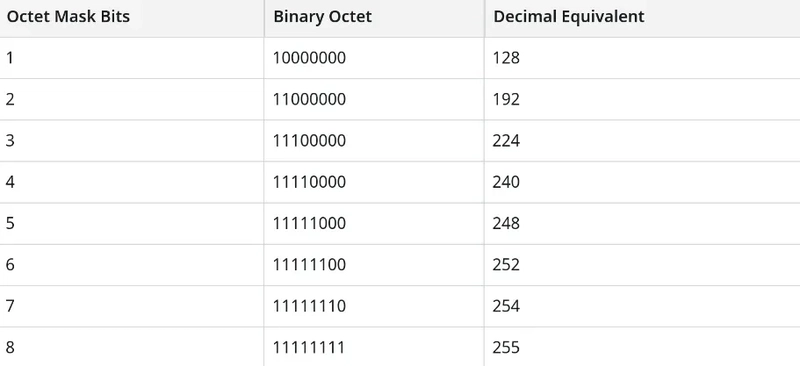
Since the ‘1’s in a mask are always contiguous, each decimal octet in a valid IPv4 mask will always be one of the following values:
0, 128, 192, 224, 240, 248, 252, 254, or 255.
Try to memorize these values to make conversions easier. For example, a mask with 14 bits would have 8 bits plus 6 bits set to 1. This would give a mask of:
11111111 11111100 00000000 00000000 which is 255.252.0.0
Host Address Ranges and Broadcasts
The purpose of subnetting is to create smaller broadcast domains with fewer hosts. The key to designing a subnet is to find the right balance between the number of subnets you need and the number of hosts per subnet. Each bit you add to the mask roughly halves the number of available host addresses.
Host Address Ranges:
- A
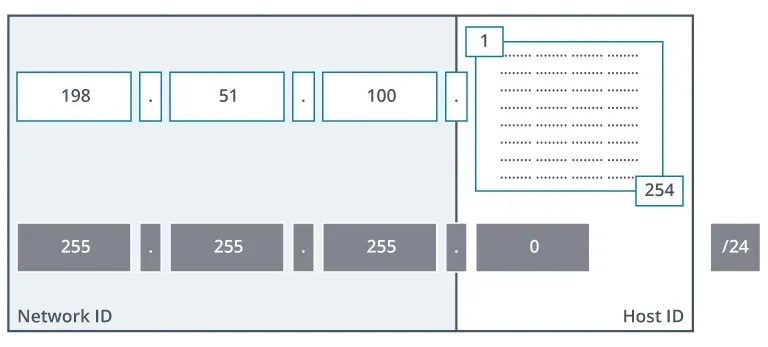
/24network (24 bits for the network ID) has 8 bits for the host ID, allowing for up to 28−2=254 usable hosts.
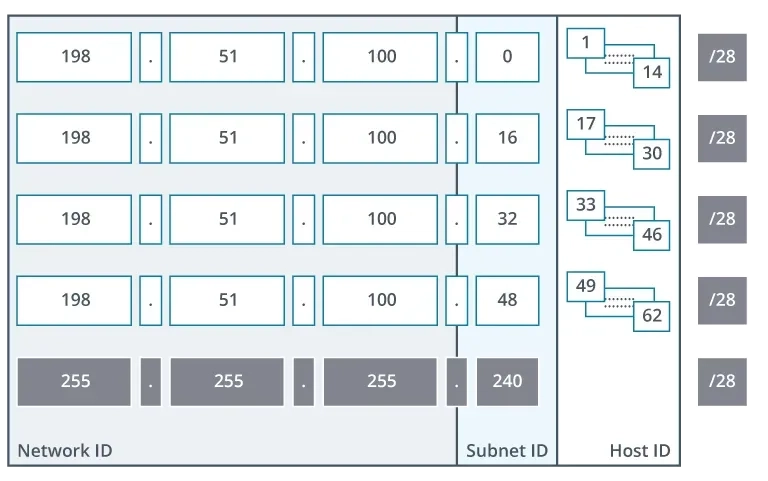
A /28 network (28 bits for the network ID) has only 4 bits for the host ID, allowing for up to 24−2=14 usable hosts.
The two addresses that are always unusable are the network address (where all host bits are 0) and the broadcast address (where all host bits are 1).
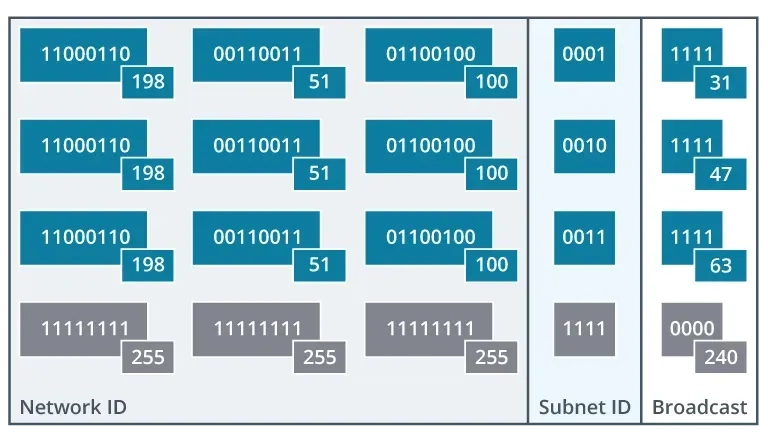
A broadcast is a packet sent to every host on a network or subnet. The broadcast address is always the last address in any network or subnet.
The Default Gateway
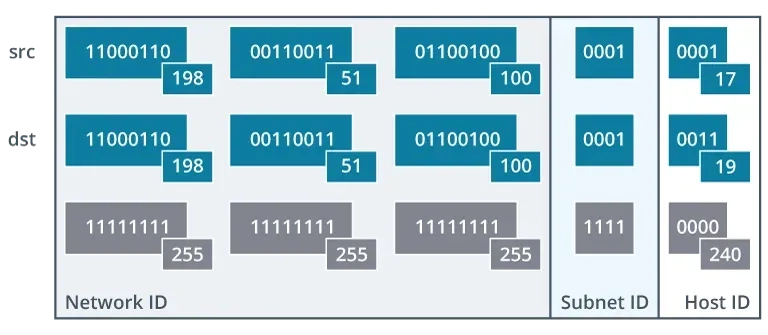
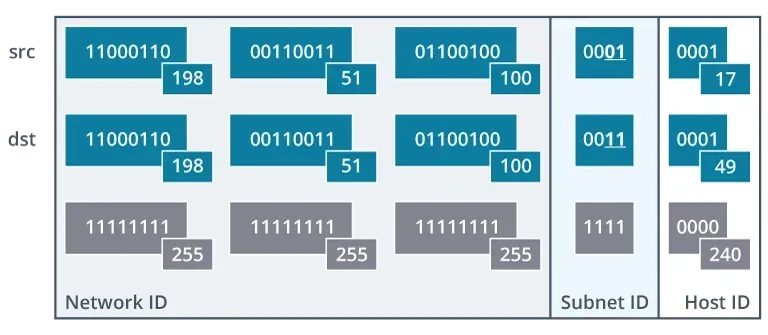
When a host wants to communicate with another device, it first checks if the destination is on its local network. It does this by comparing the Network IDs of its own IP address and the destination’s IP address.
If the network IDs match, the host knows the destination is on the same local network and sends the packet directly to it.
If the network IDs do not match, the host knows the destination is on a different network. It then sends the packet to its default gateway.
The default gateway is a router that is configured with paths to remote networks. The router then uses its own routing table to determine the best path for the packet. If the router can’t find a path, it drops the packet and notifies the host.
The IP address of the default gateway can be any usable host address, but by convention, it’s typically the first or last usable address in the subnet.
IP Interface Configuration in Windows and Linux
Every network adapter needs an IP address, a subnet mask, and a default gateway. It is also usually configured with the addresses of DNS (Domain Name System) servers, which translate domain names (like google.com) into IP addresses.
IP configuration can be static (manually assigned) or dynamic (automatically assigned by a server using DHCP).
In Windows:
- The first Ethernet adapter is usually named “Ethernet.”
- You can configure interfaces using the GUI (via the Network Connections applet or Windows Settings).
- You can also use the legacy command prompt tool
netsh.-
netsh interface ip set address "Ethernet" dhcp(sets the adapter to use DHCP) -
netsh interface ip set address "Ethernet" static 198.51.100.17 255.255.255.240 198.51.100.30(sets a static IP, mask, and gateway)
-
- For scripting, PowerShell is now preferred, using cmdlets like
Get-NetIPAddress,New-NetIPAddress, andSet-NetIPAddress.
In Linux:
- Interfaces are often named
eth0,eth1, etc. - Configuration can be different depending on the distribution.
- The persistent configuration (the one that survives a reboot) is separate from the running configuration.
- Historically, persistent settings were edited in the
/etc/network/interfacesfile usingifupandifdowncommands. - Many modern distributions use NetworkManager or
systemd-networkd. - Ubuntu, for example, uses Netplan, which simplifies configuration with YAML files.
You’ve now got a solid grasp of IPv4 addressing. The most effective way to make these concepts stick is to practice them! Grab a pen and paper, or open a calculator, and try converting a few more IP addresses from binary to decimal and back again.
As you prepare for the CompTIA Network+ exam, remember that every complex networking concept is built on these foundational ideas. Keep building on this knowledge, and you’ll be well on your way to becoming a networking pro.