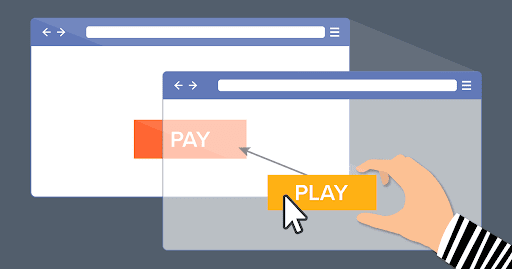
Clickjacking: Safeguarding Your Application from Invisible Threats
Clickjacking, also known as a “UI redress attack,” is a malicious technique where an attacker tricks users into clicking on something different from what they perceive. This deceptive practice can lead users to inadvertently share confidential information, enable their camera or microphone, transfer funds, or perform other unintended actions. As an application author, it is your responsibility to ensure that your users are not victims of such deceptive attacks.
In this comprehensive guide, we will explore clickjacking in detail, including how it works, real-world examples, technical implementations, defenses, and best practices to protect your application and its users.
Table of Contents
- Introduction to Clickjacking
- History and Evolution
- How Clickjacking Works
- Types of Clickjacking Attacks
- Real-World Examples
- Technical Implementation of Clickjacking
- How to Detect Clickjacking
- Defending Against Clickjacking
- Using HTTP Headers to Prevent Clickjacking
- Frame Busting Techniques
- Client-Side Protections
- Server-Side Protections
- Testing Your Application for Vulnerabilities
- Security Tools and Libraries
- Clickjacking and Regulatory Compliance
- Best Practices for Developers
- Conclusion
1. Introduction to Clickjacking
Clickjacking is a security vulnerability where a user is tricked into clicking on a hidden or disguised UI element, which could lead to unintended actions. This attack is typically implemented by embedding the legitimate application within a hidden iframe on a malicious website. The attacker overlays the iframe with transparent or opaque layers that mislead the user.
2. History and Evolution
Clickjacking was first publicly discussed in 2008 by Jeremiah Grossman and Robert Hansen. The concept has since evolved, with attackers becoming increasingly creative in how they exploit UI behavior. Early attacks targeted social media, online banking, and browser settings. As technology has advanced, so have the methods used in these attacks.
3. How Clickjacking Works
At the core, clickjacking involves embedding a webpage (the target) into an iframe and layering it beneath elements controlled by the attacker. Users think they’re interacting with the top layer, but their actions affect the hidden iframe. The attacker can manipulate the position, opacity, and z-index of HTML elements to deceive the user.
For example:
<iframe src="https://victim-site.com" style="opacity:0; position:absolute; top:0; left:0; z-index:2;"></iframe>
<button style="position:absolute; top:0; left:0; z-index:3;">Click Here to Win a Prize</button>
When the user clicks the button, they may actually be clicking on a hidden form submission button or another action in the iframe.
4. Types of Clickjacking Attacks
- Likejacking: Tricks users into liking a page on social media without their knowledge.
- Cursorjacking: Manipulates the position of the cursor, misleading users into clicking on unintended elements.
- Filejacking: Tricks users into uploading sensitive files.
- UI redress: Misleads users by altering the appearance of the user interface.
- Device access clickjacking: Gains access to webcam or microphone permissions without user intent.
5. Real-World Examples
- Facebook Likejacking: In 2010, users were tricked into liking content they never intended to.
- Adobe Flash Settings Clickjacking: Users were tricked into enabling their webcam and microphone.
- Twitter Retweet Exploit: Attackers embedded Twitter buttons and tricked users into retweeting malicious links.
6. Technical Implementation of Clickjacking
Clickjacking often uses HTML, CSS, and JavaScript to layer elements and manipulate user perception. Attackers might:
- Use iframes to load the target site.
- Set iframe opacity to 0.
- Align click targets.
- Use JavaScript to track cursor position.
- Mask legitimate UI with misleading content.
7. How to Detect Clickjacking
Detection can be challenging, but several strategies exist:
- Manually check your application in an iframe.
- Use tools like X-Frame-Options testing utilities.
- Monitor for unusual click patterns or iframe loads.
- Perform penetration testing.
8. Defending Against Clickjacking
There are multiple layers of defense, including:
- HTTP response headers.
- JavaScript frame-busting code.
- Content Security Policy (CSP).
- Restricting iframe embedding.
9. Using HTTP Headers to Prevent Clickjacking
Two headers are especially important:
- X-Frame-Options: This header has three values:
DENY: Prevents all framing.SAMEORIGIN: Allows framing only from the same origin.ALLOW-FROM uri: Allows from specific URI (limited browser support).
- Content-Security-Policy (CSP): The
frame-ancestorsdirective lets you specify who can embed your content:
Content-Security-Policy: frame-ancestors 'self' https://trustedpartner.com;
10. Frame Busting Techniques
Frame busting scripts are JavaScript snippets that detect if the application is inside a frame and then break out of it. Example:
if (top !== self) {
top.location = self.location;
}
Note: Some browsers may block or ignore this.
11. Client-Side Protections
- Use frame busting.
- Add visual clues that indicate iframe presence.
- Implement CAPTCHA or confirmation clicks.
- Use pointer-events CSS to prevent iframe interaction:
iframe {
pointer-events: none;
}
12. Server-Side Protections
- Configure HTTP headers.
- Validate referrers.
- Enforce authorization checks server-side.
- Ensure critical actions require re-authentication or confirmation.
13. Testing Your Application for Vulnerabilities
- Use browser developer tools to embed your application in an iframe.
- Employ automated security scanners.
- Conduct regular security audits.
- Engage external security experts.
14. Security Tools and Libraries
- OWASP ZAP: Open-source web application security scanner.
- Burp Suite: For advanced penetration testing.
- Clickjacking Test Tools: Online utilities that test X-Frame-Options/CSP headers.
15. Clickjacking and Regulatory Compliance
Many data protection regulations like GDPR, HIPAA, and PCI-DSS require secure handling of user actions and prevention of unauthorized access. Clickjacking prevention is essential for compliance:
- Protects user consent integrity.
- Prevents data leakage.
- Demonstrates proactive security posture.
16. Best Practices for Developers
- Always set
X-Frame-OptionsorContent-Security-Policyheaders. - Avoid embedding sensitive pages in iframes.
- Require user confirmation for critical actions.
- Educate team members about UI redress risks.
- Use modern frontend frameworks with built-in security.
17. Conclusion
Clickjacking remains a potent threat in the modern web security landscape. As an application developer, you have a duty to protect your users from deception and malicious manipulation. By implementing layered defenses—headers, scripts, client- and server-side checks—you can create a secure environment that inspires trust. Regular testing, security reviews, and adherence to best practices ensure your application stays protected from evolving threats.
Remember: a secure UI is not just a feature—it’s a responsibility.
Stay secure, code smart.