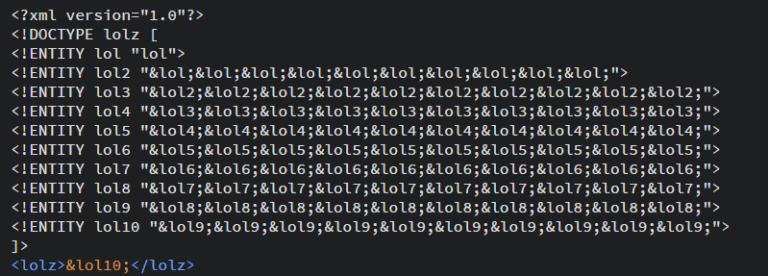
Understanding XML Bombs: A Deep Dive into Vulnerabilities, Attacks, and Prevention
Table of Contents 1. Introduction to XML and Its Role in Modern Applications Extensible Markup Language (XML) is a widely-used format for exchanging structured data across different systems. From configuration files to web services and SOAP APIs, XML plays a critical role in numerous applications. However, its flexibility can become a double-edged sword. Improperly handled…