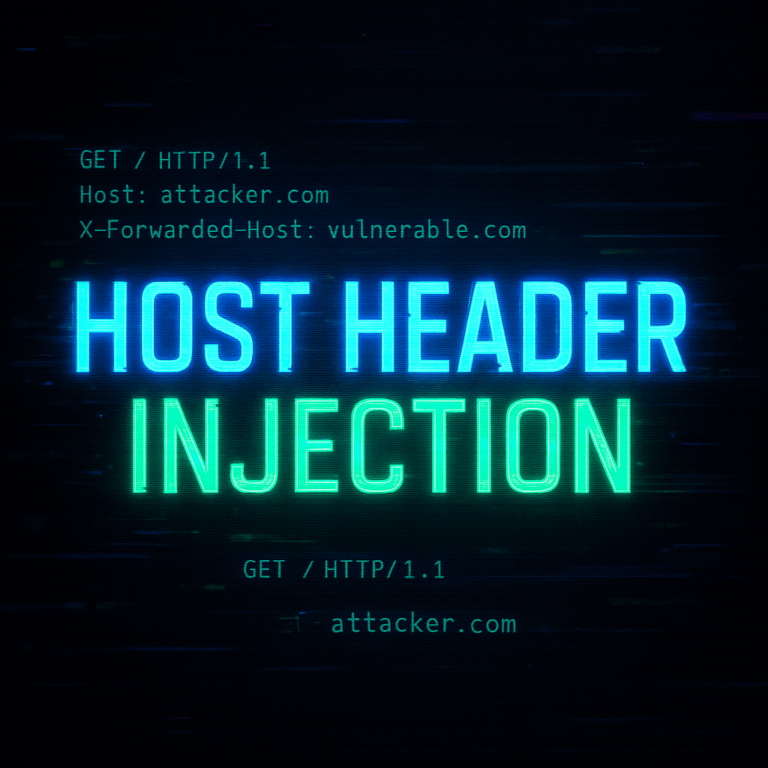
Host Header Poisoning: A Hidden Threat in Web Security
Introduction In the evolving landscape of web application security, many threats go unnoticed or underestimated. One such silent attacker is Host Header Poisoning. Although it doesn’t make headlines like SQL Injection or Cross-Site Scripting (XSS), Host Header Poisoning can lead to serious vulnerabilities in web applications, including cache poisoning, password reset poisoning, virtual host routing…