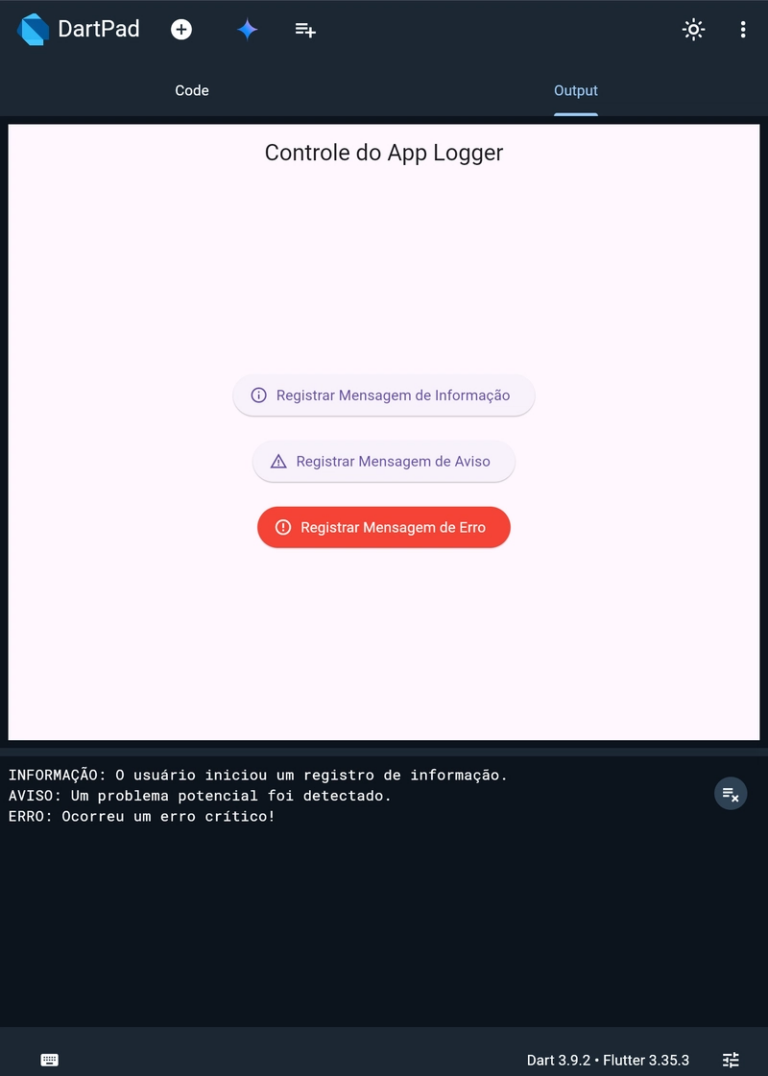
Observabilidade em aplicações móveis
Observalidade é um conceito importante no desenvolvimento de aplicações móveis, servindo para acompanhar a saúde do sistema, ajudando a identificar problemas mais rápido, facilitando o entendimento de um fluxo entre outros. Dentro da observabilidade temos logs, alertas entre outros conceitos, sendo os dois primeiros abordados a seguir. Logs Os logs nos trazem algum tipo de…