Walmart has an RTX 5070 gaming PC on sale for $1,099 right now – yep, really
Walmart has just slashed the price on this RTX 5070 gaming PC by an eye-watering $800.

Walmart has just slashed the price on this RTX 5070 gaming PC by an eye-watering $800.

The petition to scrap the plan to introduce mandatory digital ID cards has garnered over one million signatures so far, as critics warn of “mass surveillance” risks.

Article also available over here as well. For the longest time I’ve used iTerm2 as a replacement for Terminal. It’s fast, it’s native, it’s not yet another lipstick-on-an-Electron-wrapper type of thing. Only Ghostty comes close to it, and even though it’s faster and resizes better, it misses some of the features I’ve grown to depend…
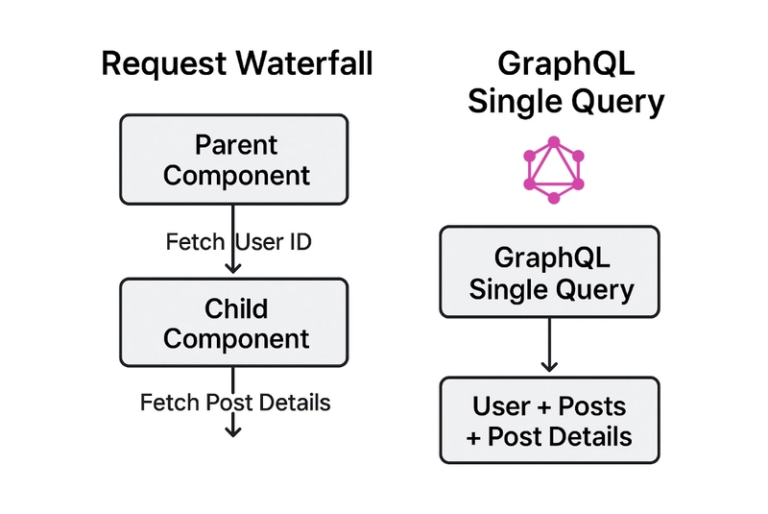
If you’ve architected a modern application in the last five years, you’ve likely hit this wall: your elegantly designed Representational State Transfer (REST) API starts creaking under the weight of real-world requirements. The mobile team needs lighter payloads. The web team wants richer data in fewer round-trips. The new dashboard demands information on six services….

How I built a comprehensive Gmail command-line interface with security-first design, Docker containerization, and CI/CD automation. 🎯 The Problem As developers, we live in our terminals. We manage code, deploy applications, and debug issues all from the command line. But when it comes to email management, we’re forced to switch to web browsers or desktop…

All the ways to watch United Rugby Championship 2025/26 live streams online from anywhere for FREE, as Ireland, Scotland, Wales, Italy and South Africa’s top clubs do battle.

Apple TV+ will feature the first MLB baseball game to use a set of iPhones as part of its broadcast equipment.

Peacemaker season 2’s latest big cameo is another with ties to Superman, and it’s one I didn’t see coming.

Big Tech is giving students free AI tools today, but the real play is loyalty tomorrow—and the companies who act now will own the next decade. Students get powerful tools and fast credentials. Companies get early trust and a steady talent pipeline. If you sit this out, you recruit from the sidelines later. This is…
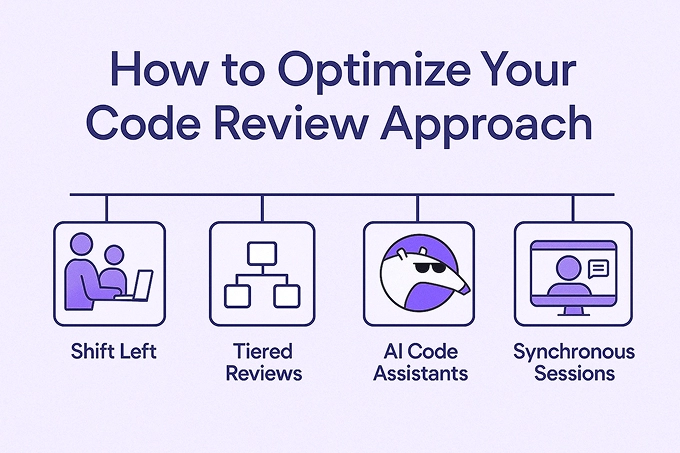
You have seen senior developers who somehow catch critical bugs that everyone else misses. They spot design flaws before they become architectural nightmares. The secret isn’t superhuman coding skills. It’s the 5-3-1 code review system. Most developers treat code reviews like a checkbox activity. Senior developers understand they are the last line of defense against production…