OAuth Misconfiguration in Symfony Explained
OAuth is a critical component in modern authentication systems. While Symfony provides robust tools for integrating OAuth through bundles like HWIOAuthBundle or Symfony UX, developers often unintentionally introduce misconfigurations that open up security vulnerabilities.
In this post, we’ll explore real-world OAuth misconfiguration scenarios in Symfony, complete with code samples, fixes, and how to test your implementation using our Website Vulnerability Scanner online free.
🔗 Also, check out our main blog at Pentest Testing Blog for more developer-centric security tutorials.
🔍 What is OAuth Misconfiguration?
OAuth misconfiguration occurs when OAuth flows (Authorization Code, Implicit, Client Credentials, etc.) are improperly implemented, exposing apps to attacks like:
- Authorization Code Interception
- Open Redirects
- Missing or incorrect scopes
- Insecure redirect URIs
- Unvalidated JWT tokens
- Lack of state parameter validation
🧠 Real Example: Misconfigured Redirect URI in Symfony
One of the most common vulnerabilities is allowing wildcards or dynamic redirect URIs without validation.
Here’s an example of a vulnerable configuration:
# config/packages/hwi_oauth.yaml
hwi_oauth:
firewall_name: main
resource_owners:
google:
type: google
client_id: '%env(resolve:GOOGLE_CLIENT_ID)%'
client_secret: '%env(resolve:GOOGLE_CLIENT_SECRET)%'
redirect_uri: '%env(resolve:GOOGLE_REDIRECT_URI)%'
Problem: If the GOOGLE_REDIRECT_URI is user-controlled or overly permissive (e.g., allowing wildcards like https://*.evil.com), an attacker can redirect tokens to malicious domains.
✅ How to Fix It
Always hard-code and validate redirect URIs.
hwi_oauth:
resource_owners:
google:
redirect_uri: 'https://yourdomain.com/login/check-google'
Also, make sure your firewall routes match and validate the redirect logic in your controller.
🛡️ Add State Parameter Verification
The state parameter prevents CSRF attacks during OAuth flows. By default, HWIOAuthBundle does not enforce state checks. Add this manually:
public function connectAction(Request $request)
{
$session = $request->getSession();
$state = bin2hex(random_bytes(32));
$session->set('oauth_state', $state);
return $this->redirect('https://accounts.google.com/o/oauth2/auth?' . http_build_query([
'client_id' => $this->getParameter('google_client_id'),
'redirect_uri' => 'https://yourdomain.com/login/check-google',
'response_type' => 'code',
'scope' => 'email profile',
'state' => $state,
]));
}
And then validate on the callback route:
public function loginCheckAction(Request $request)
{
$state = $request->query->get('state');
$sessionState = $request->getSession()->get('oauth_state');
if ($state !== $sessionState) {
throw new AccessDeniedHttpException('Invalid state parameter');
}
// Continue login...
}
🧪 Detect OAuth Misconfigurations Automatically
To validate your Symfony app’s OAuth flow and other security misconfigurations, use our free Website Vulnerability Scanner.
🖼️ Screenshot of the Website Vulnerability Scanner Page:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
It detects common issues like:
- Open Redirects
- Missing state parameter
- Exposed client secrets
- Insecure callback URLs
- Leaky access tokens
🖼️ Sample Report from the Tool to check Website Vulnerability:
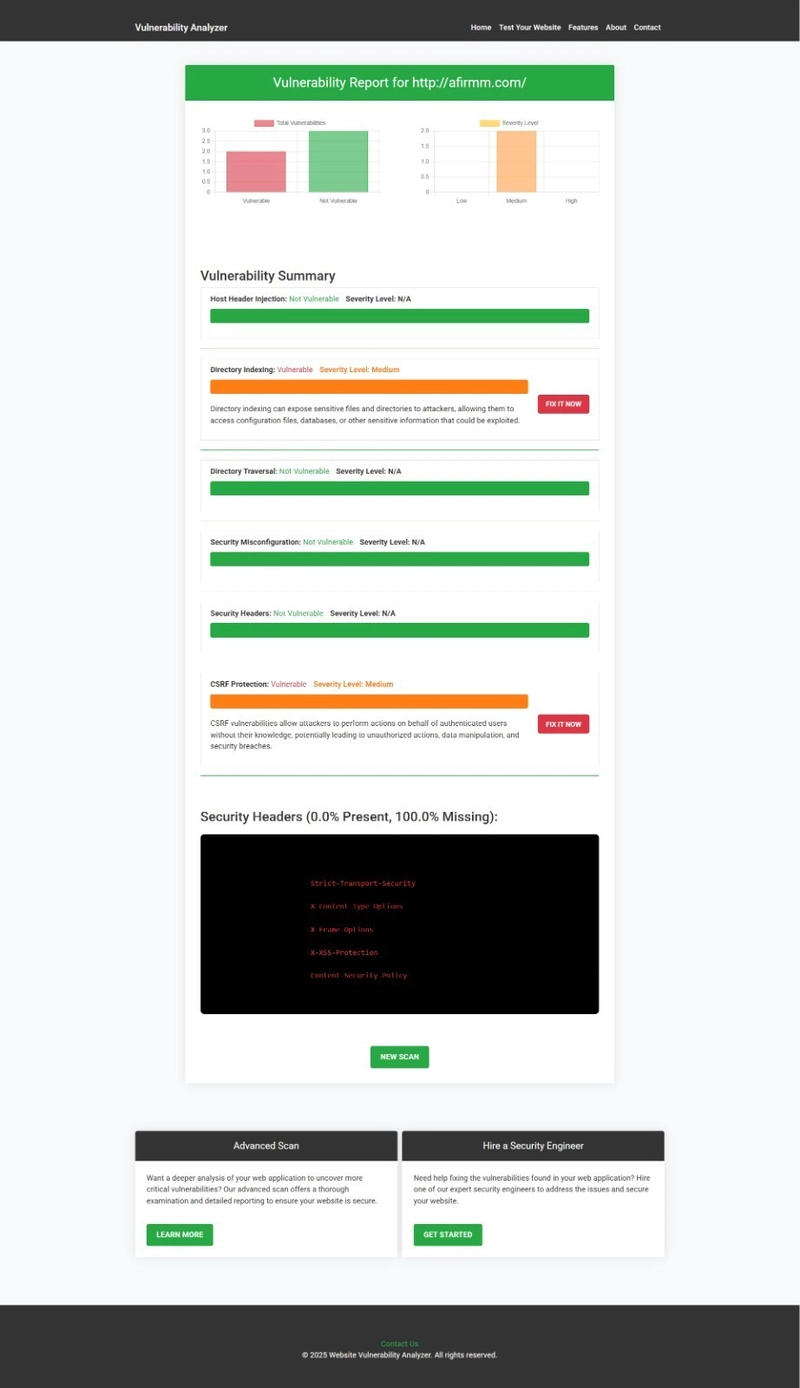 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Try it at 👉 https://free.pentesttesting.com/
📦 Bonus: Token Signature Validation in Symfony
JWT tokens returned by OAuth providers (like Google or GitHub) should be verified before trusting them.
Example of insecure usage:
// Don't just decode JWTs without verifying the signature!
$decoded = JWT::decode($token, null, false);
Safe implementation:
use FirebaseJWTJWT;
use FirebaseJWTJWK;
// Fetch keys from Google's JWKs URI
$jwks = json_decode(file_get_contents('https://www.googleapis.com/oauth2/v3/certs'), true);
$keys = JWK::parseKeySet($jwks);
// Validate signature
$decoded = JWT::decode($id_token, $keys, ['RS256']);
Ensure you check:
- Issuer (iss)
- Audience (aud)
- Expiry (exp)
🤝 Partner With Us or Offer Cybersecurity to Your Clients
Are you a dev agency or security professional? Collaborate with us.
🔗 Offer Cybersecurity Services to Your Clients
Looking to protect your AI-driven apps?
🔗 AI Application Cybersecurity Services
📬 Stay Updated on Security Trends
Subscribe to our growing LinkedIn newsletter for free weekly insights, CVE coverage, and exclusive offers.
👉 Subscribe on LinkedIn: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🔚 Final Thoughts
OAuth is powerful but tricky. Symfony developers need to stay vigilant against subtle configuration oversights that could lead to major security breaches.
Scan your app with our free tool for a Security test, and follow best practices in redirect URI handling, token validation, and state parameter usage.
For more deep dives like this, visit our blog at https://www.pentesttesting.com/blog/
Want a free scan? DM us or check https://free.pentesttesting.com/