🚨 “Google Alert: Someone Just Logged In?” — Don’t Fall for the Phishing Trap
title: “How a Fake Email Can Fool Anyone — And How You Can Stay One Step Ahead”
🛡️ “Cybersecurity is not just a tech issue — it’s a human issue. Awareness is your first defense.”
By Shubhra 📅 9 July 2025 • 🕒 7 min read
🧩 A Real Case: Google Login Phishing Email
It looked like a normal alert from Google.
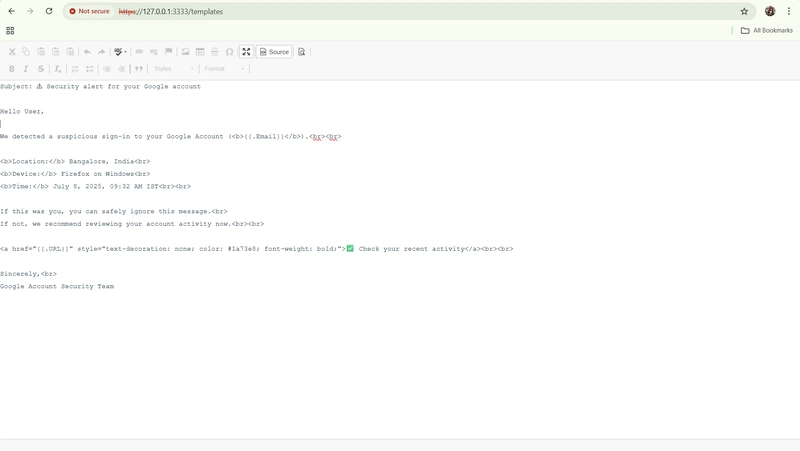
- Subject: ⚠ Security alert for your Google account
- Location: Bangalore, India
- Time: July 8, 2025
“We detected a suspicious sign-in to your Google Account. If this wasn’t you, review your activity now.”
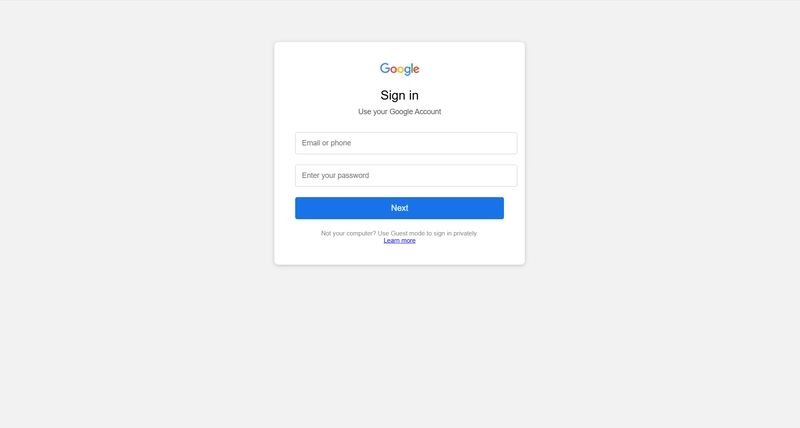
The button said “Check your activity,” leading to a near-perfect Google login screen.
But it was fake.
A phishing page created to steal your credentials.
This wasn’t an accident. It’s a real, effective scam used worldwide every day.
🧠 What is Phishing?
Phishing is a type of cyberattack where attackers impersonate trusted services like Google or your bank to:
- Trick you into clicking malicious links
- Capture sensitive info (username, passwords, OTPs)
- Install malware or commit fraud
🎯 The ultimate goal? Steal access, money, or data.
🔍 How Are Scammers Able to Pull This Off?
Here’s why phishing works so well:
- 🎭 Brand mimicry: Logos, layout, and language match real emails.
- ⚠️ Urgency: “Suspicious login detected” makes you panic-click.
- 🔗 Fake login pages: Look just like the real thing.
- 🤖 AI tools: Scammers can build these in minutes.
- 🕵️ Instant data capture: You enter info — they steal it.
It’s quick, polished, and scarily effective.
💻 How Do Phishing Scams Work?
Let’s recreate the above case with a real (safe) simulation using GoPhish and Mailtrap.
⚙️ Step 1: Crafting the Fake Email
Scammers design emails with:
- Realistic Google fonts, colors, and logos
- Alarming messages like “Your account was accessed”
- A strong CTA like “Check your activity”
🧠 They rely on fear + urgency = impulsive action
⚙️ Step 2: Fake Login Page Setup
The link goes to a fake Google login:
- Hosted at
g00gle-alert.com(looks legit but isn’t) - Styled exactly like Google’s real page
- Captures everything typed in
Once submitted:
- The attacker receives your credentials
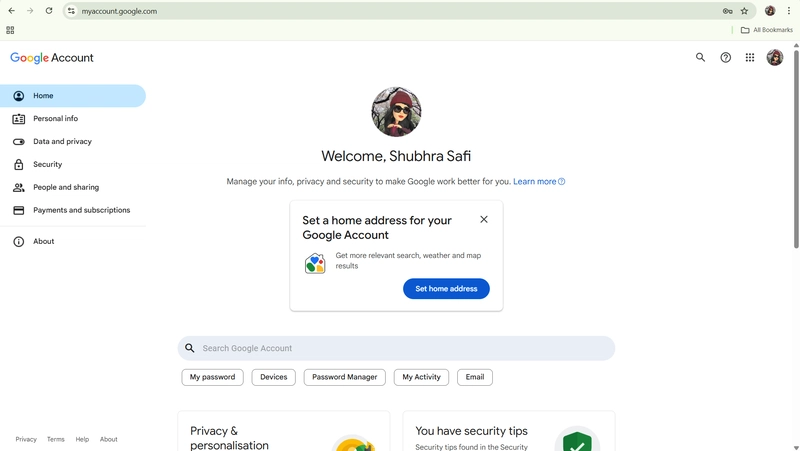
- You may be redirected to the real Google login to avoid suspicion
⚙️ Step 3: Harvesting Credentials
Now the attacker has:
- Your email
- Your password
- Device/IP information
If you reused that password? Game over.
Now let’s send the mail to a user and check the complete process.
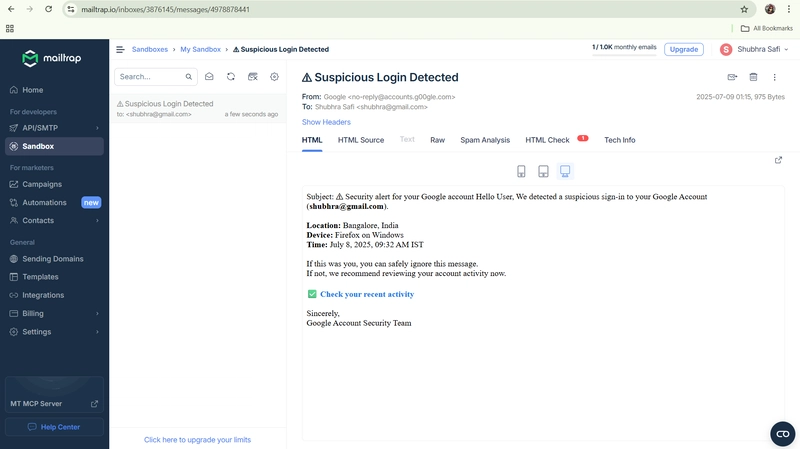
User receives the mail in their mailbox.
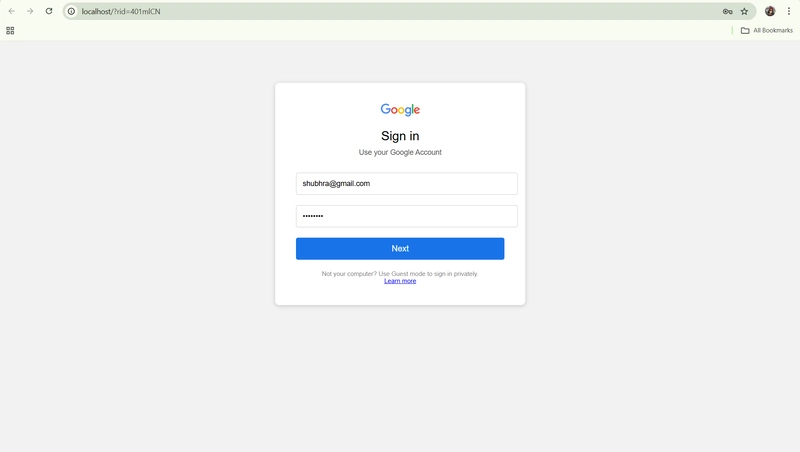
User clicks the link and lands on the fake login page, enters the credentials and is actually redirected to real google account page.
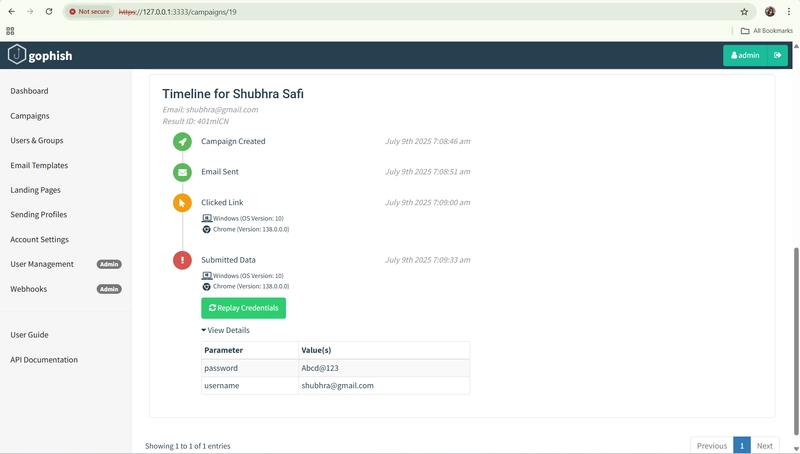
*While on the backend the scammer receives the complete details like the credentials of the user, device info, browser info, OS info. *
🛡️ How to Spot a Phishing Email
| ✅ Red Flag | 🚫 What to Watch |
|---|---|
| Suspicious sender | no-reply@goog1e-security.com |
| Generic greeting | “Hi user” instead of your name |
| Urgent tone | “Click NOW or lose access!” |
| URL mismatch | Hover reveals strange link |
| Bad formatting | Typos or broken layout |
🔐 How to Protect Yourself
Six simple ways to stay safe:
- 🔍 Check sender domains
- 🖱️ Hover over links before clicking
- 🧠 Don’t panic — scams rely on emotion
- 🔐 Enable 2FA/MFA
- 🧩 Use a password manager
- 🚨 Report suspicious messages
🧠 Final Thoughts
Phishing attacks today are:
- Polished
- Convincing
- Automated with AI
- Constantly evolving
They aren’t obvious. They’re smart — and they’re coming for you.
“Think before you click — your identity depends on it.”
✍️ Author’s Note
This post was created as a simulated phishing attack using ethical tools for awareness only.
No real accounts or users were compromised.
The goal is simple: If one person avoids getting scammed after reading this, it worked.
Please share it. Teach others. Spread awareness.
🔐 Stay Alert. Stay Informed. Stay Phish-Free.
💬 What’s Your Take?
Have you seen a convincing phishing email?
Got tips of your own to share? Drop them in the comments 👇